
XML-RPC is a remote procedure call protocol that allows anyone to interact with your WordPress website remotely. In other words, it’s a way to manage your site without having to log in manually via the standard “wp-login.php” page. It’s widely used by plugins, most famously by Automattic’s own Jetpack plugin. These days, however, the word “XML-RPC” has gotten a bad name. In this tutorial, we will explain what is WordPress XML-RPC and how to stop an XML-RPC attack on your WordPress website.
Table of Contents
Is XML-RPC Enabled on Your WordPress Website?
A quick way to check if your site is vulnerable is to visit the following URL from a browser:
yoursite.com/xmlrpc.php
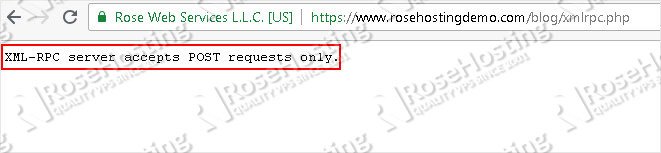
If it’s enabled, you should get a response that says “XML-RPC server accepts POST requests only.” Like this:
The Dangers and Benefits of XML-RPC
There’s been a lot of back and forth in the WordPress security community about XML-RPC. There are mostly two concerns:
- XML-RPC can be used to DDoS a site
- It can be used to repeatedly try username/password combinations
At least, these were possible. WordPress has since plugged loopholes that allowed people to try hundreds of usernames and passwords at once. Since version 4.4, it’s been quite improved. Now WordPress will silently fail all subsequent login attempts as soon as a single XML-RPC call has failed. Great!
However, there are those who are still concerned about the ease by while remote procedure calls like this can be made. So here are a few ways to secure your site against XML-RPC – starting from the lightest touch to the heaviest.
Method 1: Disable Pingbacks
This is a process that uses your server as an unwitting participant in an attack against another server. Basically, someone tells your site “Hey, this URL linked to your blog!” And then your site responds with a “pingback” to that URL. Except that there’s no verification that the URL actually did link back to you. Do this with hundreds of vulnerable WordPress sites, and you have a DDoS attack on your hands! The easiest way to prevent your site from being used in this manner is to add the following code to your theme’s functions.php:
function stop_pings ($vectors) {
unset( $vectors['pingback.ping'] );
return $vectors;
}
add_filter( 'xmlrpc_methods', 'stop_pings');
Method 2: Prevent All Authentication Requests via XML-RPC
This second method determines whether you want to allow XML-RPC methods that authenticate users. Take for example, publishing a blog via e-mail. The site will receive your e-mail, authenticate you via XML-RPC, and then publish it if the credentials match.
A lot of people are uncomfortable with the ability of XML-RPC to just take in random calls like this. It’s what led to hundreds or thousands of authentication attempts in the first place. Even though WordPress has since addressed this particular form of hacking, there are those who recommend simply turning it off.
To do that, enter this code in functions.php:
add_filter('xmlrpc_enabled','__return_false');
It’s important to note that this is not the same as the first method. This code only disables authentication methods and leaves all others untouched – like pingbacks for example.
Method 3: Disable Access to xmlrpc.php
This is the most extreme method that completely disables all XML-RPC functionality. It requires you to edit the .htaccess file at the root of your WordPress directory. Add the following code to the top:
<files xmlrpc.php> Order allow,deny Deny from all </files>
Note: If you find your WordPress installation doesn’t have a .htaccess file at its root folder, simply create one with the following default code.
# BEGIN WordPress
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^index\.php$ - [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L]
</IfModule>
# END WordPress
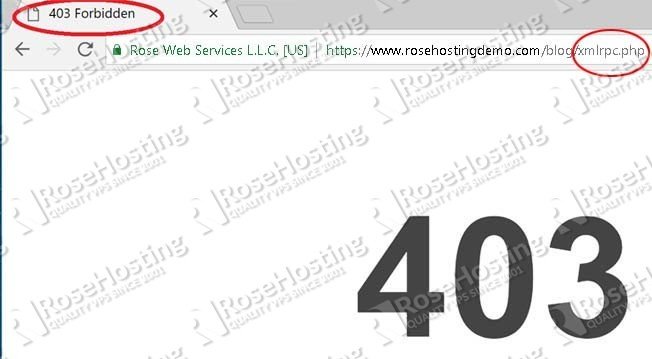
Now with the above denial rules in effect, trying to access xmlrpc.php will be met with the following page:
And that’s all there is to it. You have successfully disabled XML-RPC altogether, on your WordPress Site.

If you use one of our Managed WordPress Hosting Services, you can simply ask our expert Linux admins to disable XML-RPC for you. They are available 24×7 and will take care of your request immediately.
PS. If you liked this post – What Is WordPress XML-RPC and How to Stop an Attack, please share it with your friends on the social networks using the buttons below or simply leave a comment in the comments section. Thanks.

You can generate 403 Denied error in WordPress too, with same plugin:
https://wordpress.org/plugins/disable-xml-rpc-littlebizzy/
If you cannot edit the htaccess file.
this plugin is not available for now